This is the third article of the Security of Server-Side Synchronization blog series. In the previous articles, we covered how server-side synchronization (SSS) authenticates with Microsoft Exchange Online and some different configurations that can be used to restrict what information SSS processes from a user’s Microsoft Exchange Online mailbox.
SSS is continuously connecting to configured Dataverse users’ Exchange mailboxes and checking to see if there are any new or updates to activities to synchronize with Dataverse. In this article, we cover how you can view this type of information using Microsoft Purview.
Once you have set up and configured Microsoft Purview, you will review the activity of SSS within the Purview audit logs. At this point, you can see what messages were included during a synchronization cycle, what messages were sent, and finally, appointments, contacts, and tasks that were synchronized.
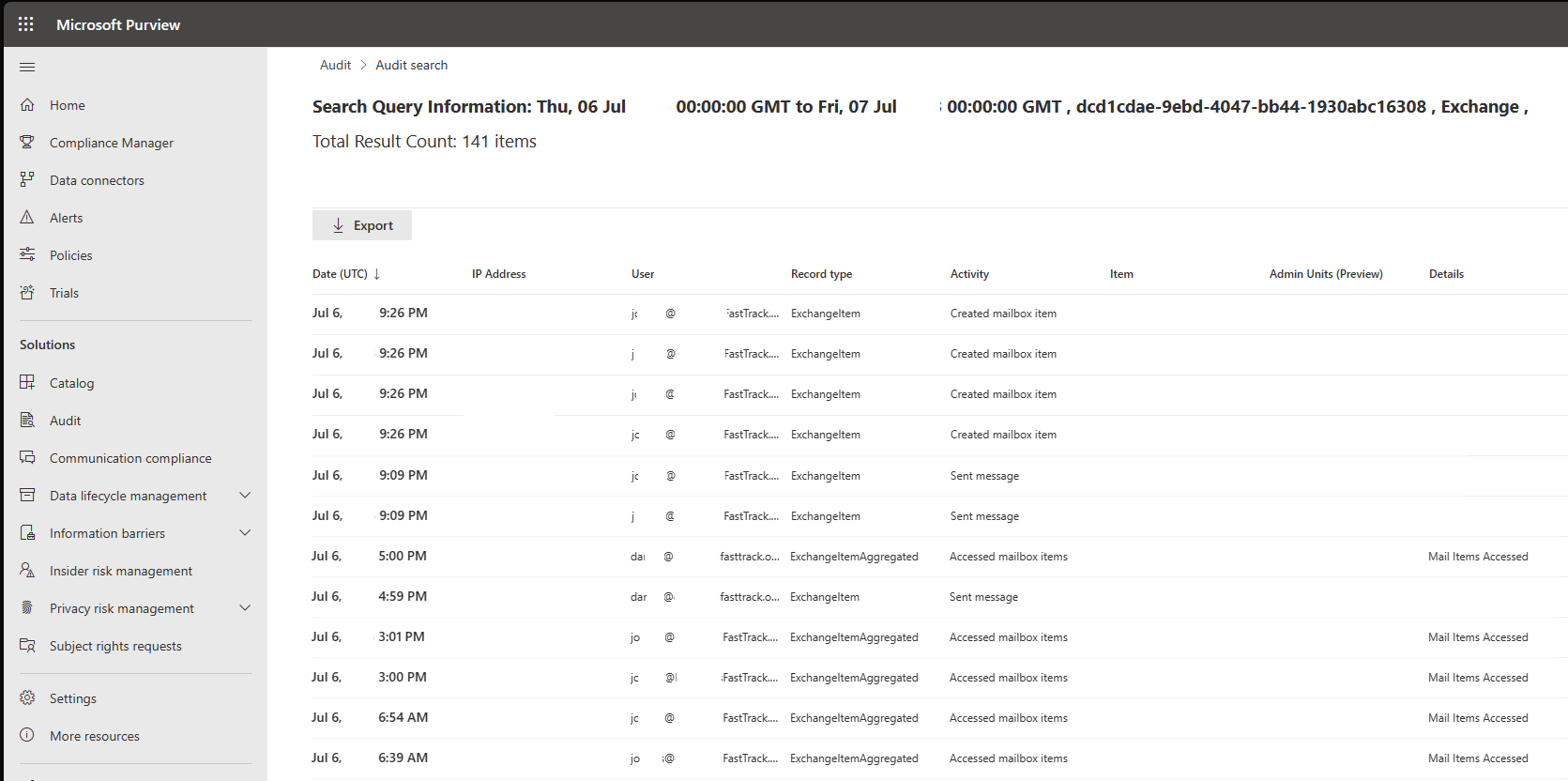 In order to easily review the activity of SSS, you will want to configure your search based on the Azure AD app id being used for SSS. The Azure AD app registration for the default Exchange Online mail server profile within Dataverse has an App ID of:
00000007-0000-0000-c000-000000000000
This is nestled deep within some documentation that doesn’t ever easily call out the SSS App ID. However, you can find it within this section of the Connect Customer Engagement (on-premises) to Exchange Online document:
Configure server-based authentication
In order to easily review the activity of SSS, you will want to configure your search based on the Azure AD app id being used for SSS. The Azure AD app registration for the default Exchange Online mail server profile within Dataverse has an App ID of:
00000007-0000-0000-c000-000000000000
This is nestled deep within some documentation that doesn’t ever easily call out the SSS App ID. However, you can find it within this section of the Connect Customer Engagement (on-premises) to Exchange Online document:
Configure server-based authentication
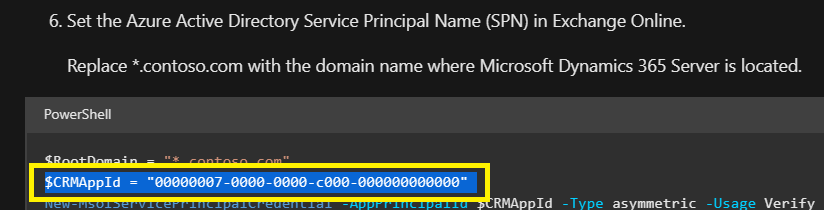 The following search options will give you the results of what SSS did during the search time frame:
The following search options will give you the results of what SSS did during the search time frame:
- Keyword Search: <AzureADAppId>
- For the default Exchange online profile, it is: 00000007-0000-0000-c000-000000000000
- Workload: Exchange
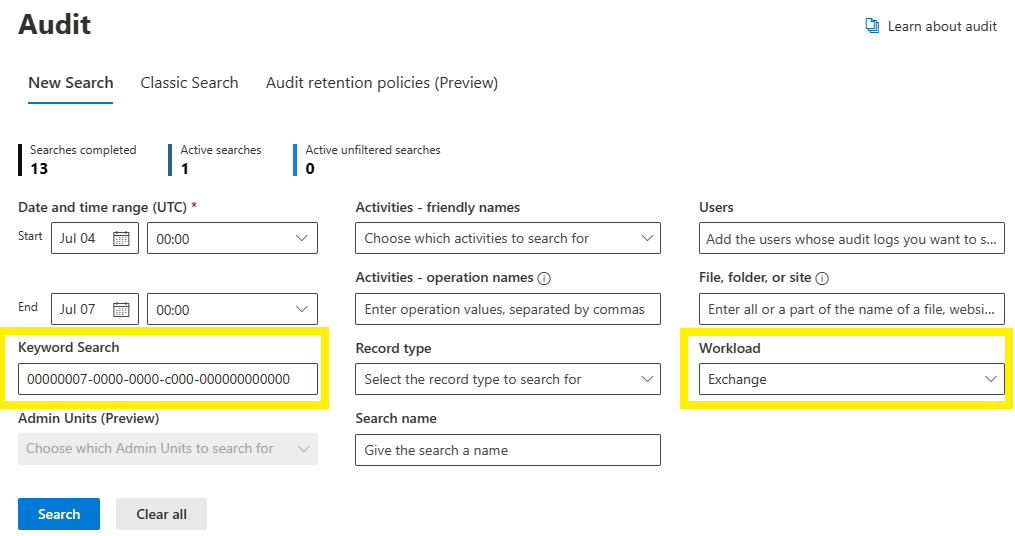 Purview provides admins the ability to monitor what Microsoft Exchange activities that were accessed by SSS. However, be sure to understand the retention policies of this data for your licensing of Microsoft Purview.
In the final article of this series, we will cover how you can further restrict server-side synchronization access to user Microsoft Exchange Online mailboxes using the cross-tenant configuration, even when SSS and Microsoft Exchange are within the same tenant.
Purview provides admins the ability to monitor what Microsoft Exchange activities that were accessed by SSS. However, be sure to understand the retention policies of this data for your licensing of Microsoft Purview.
In the final article of this series, we will cover how you can further restrict server-side synchronization access to user Microsoft Exchange Online mailboxes using the cross-tenant configuration, even when SSS and Microsoft Exchange are within the same tenant.
See the other articles of this blog series:



