Dataverse Managed Environments Deep Dive:
What is Managed Environments ?
Managed environments is a set of features that allows administrators to manage Power Platform at scale with more control, less effort, and more visibility.
List of features available with Managed Environments for now (18/09/24) :
- Limit sharing
- Weekly usage insights
- Data policies
- Pipelines in Power Platform (preview)
- Maker welcome content (preview)
- Solution checker
- IP Firewall
- IP cookie binding
- Customer Managed Key (CMK)
- Lockbox
- Extended backup
- DLP for desktop flow
- Export data to Azure Application Insights
- Catalog in Power Platform
- Default environment routing
- Create an app description with Copilot
- Virtual Network support for Power Platform
Requirements to enable Managed Environments
You may ask why to not activate this option on every environments ? What are the requirements and implications of enabling Managed Environments.
Everything is about licensing, when activating Managed Environments, every user that want to access the resources (Power Apps, Power Automate, Power Virtual Agents, and Power Pages website) in this environment must have a standalone licenses, Dynamics 365 Enterprise license or capacity add-ons.
Example of which licenses cannot run app in Managed Environments:
- Microsoft/Office 365 licenses (Business, E1, E3, E5, F1, F3, …) that are coming with access to some limited Power Apps, Power Automate capabilities.
How to enable/disable Managed Environments ?
Permissions required
- You must have the role of global admin, Power Platform service admin, or Dynamics 365 admin Microsoft Entra ID.
- Any user with permission to see environment details can consult the Managed Environments property for an environment (from the list).
Users with the Delegated Admin role or the Environment Admin security role aren't allowed to change the Managed Environments property in an environment.
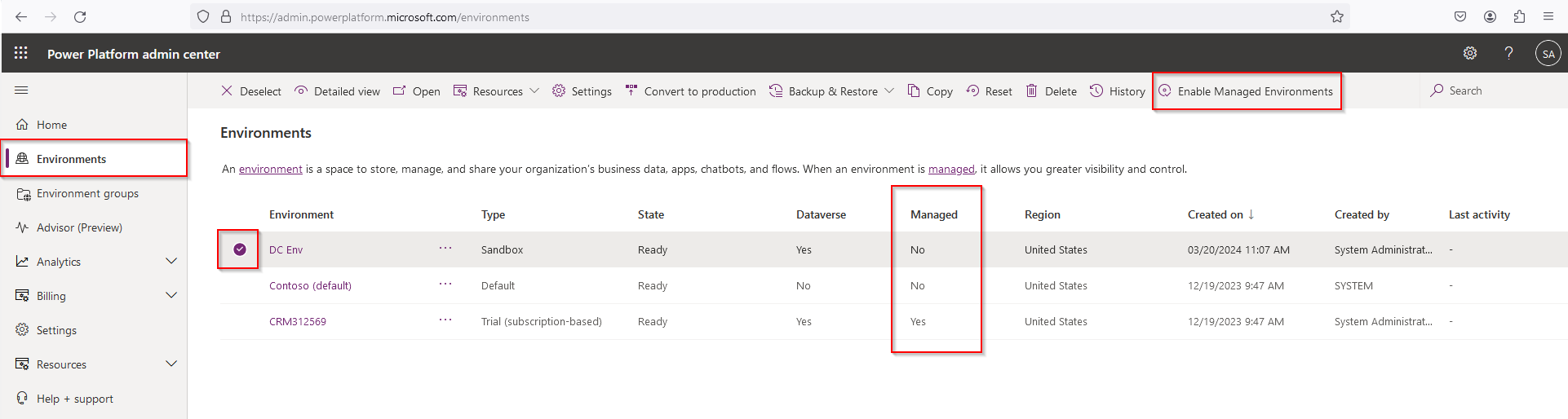
Enable Managed Environments in the admin center
Open the Power Platform admin center.
Enable Managed Environments using PowerShell
Below the script to enable Managed Environments (don't forget to replace , it can be found here https://admin.powerplatform.microsoft.com) :
$GovernanceConfiguration = [pscustomobject] @{
protectionLevel = "Standard"
settings = [pscustomobject]@{
extendedSettings = @{}
}
}
Set-AdminPowerAppEnvironmentGovernanceConfiguration -EnvironmentName -UpdatedGovernanceConfiguration $GovernanceConfiguration
Copy Managed Environment settings using PowerShell
These commands can be useful for deploying Managed Environments settings from one environment to another one. If the target environment wasn't a Managed Environment, copy settings will also enable it as a Managed Environment.
#Get settings from the source Managed Environment
$sourceEnvironment = Get-AdminPowerAppEnvironment -EnvironmentName
# Copy the settings from the source Managed Environment above to the target environment
Set-AdminPowerAppEnvironmentGovernanceConfiguration -EnvironmentName -UpdatedGovernanceConfiguration $sourceEnvironment.Internal.properties.governanceConfiguration
Disable Managed Environments using PowerShell
Managed Environments can be disabled by administrators using PowerShell. Before disabling Managed Environments, the administrator must ensure that none of the Managed Environments capabilities are in use.
Below the PowerShell script to disable Managed Environments :
$UpdatedGovernanceConfiguration = [pscustomobject]@{
protectionLevel = "Basic"
}
Set-AdminPowerAppEnvironmentGovernanceConfiguration -EnvironmentName -UpdatedGovernanceConfiguration $UpdatedGovernanceConfiguration
Quick overview of the available features
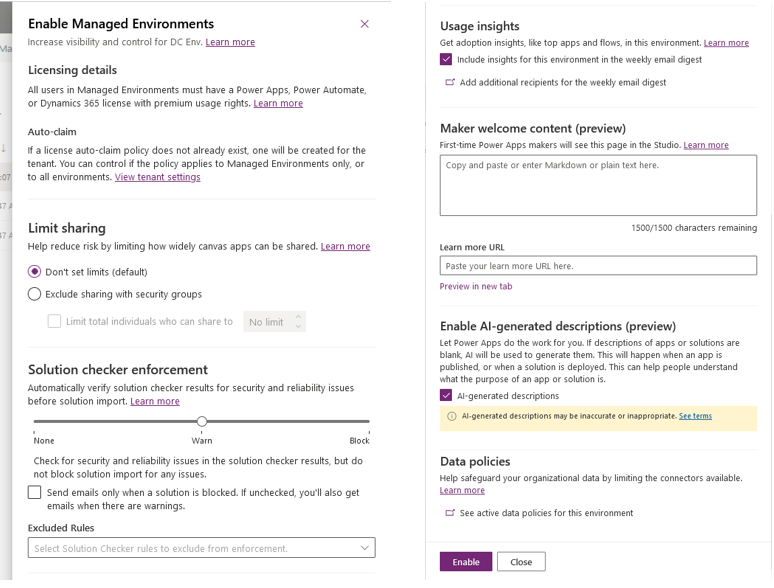
Limit sharing
Canvas app can be shared with users. With this feature, admins can limit how broadly users can share canvas apps. It is possible to restrict sharing with security groups and also set a limit on the number of individuals with whom the app can be shared.
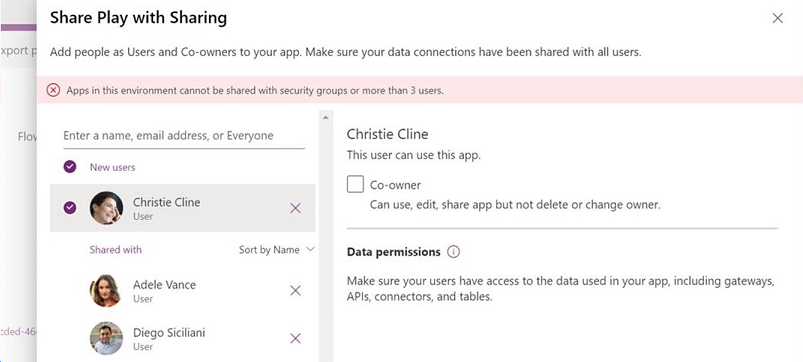
Here is what the user will see when trying to share an app that is not matching the limit sharing rule:
Usage Insights
Keep updated on the status of your managed environments with Power Platform's weekly admin digest. Receive analytics detailing your top apps, most influential makers, and inactive resources that can be safely cleaned up, all conveniently delivered to your mailbox every week.
Here is the setting to enable Usage Insights (please note that also need to enable tenant-level analytics to get usage insights):
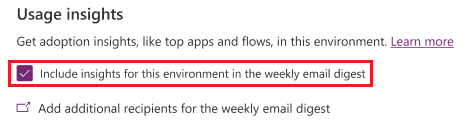
Who will receive the weekly digest ?
The weekly digest is sent to all users with the roles of Power Platform administrator and Dynamics 365 service administrator.
To include more recipients, choose "Add additional recipients for the weekly email digest", then opt for "Weekly digest" and input email addresses into the "Additional recipients" box.
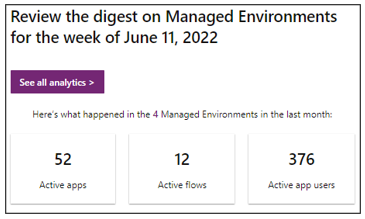
What information is presented in the weekly digest ?
The first part of the weekly digest shows the number of apps used and active users in your managed environments in the past month.
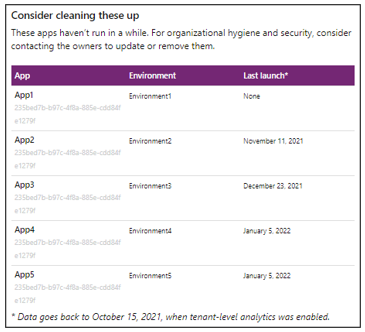
The second part of the weekly digest shows lists apps and flows that haven't been launched in a while. The last launch column shows the last date of use for the app or flow. If an app or flow isn't being used, we recommend that you work with its owner to update or remove it.
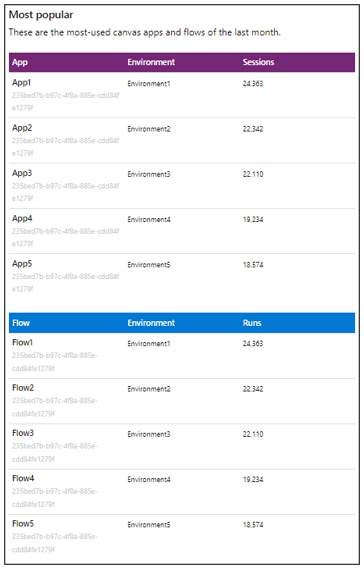
The third part of the weekly digest shows the most popular apps and flows in your managed environments in the past month, indicated by the number of sessions and runs. When a user launches and interacts with an application, that's considered a session.
Data Policies
With this feature, admins can easily identify all the data policies that are applied to an environment.
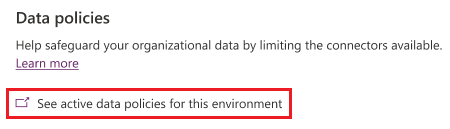
When clicking on "See active data policies for this environment", the data policies page opens in a new tab. The view is filtered to display only the data policies that are applied to the managed environment. The environment filter is exclusively available for managed environments.
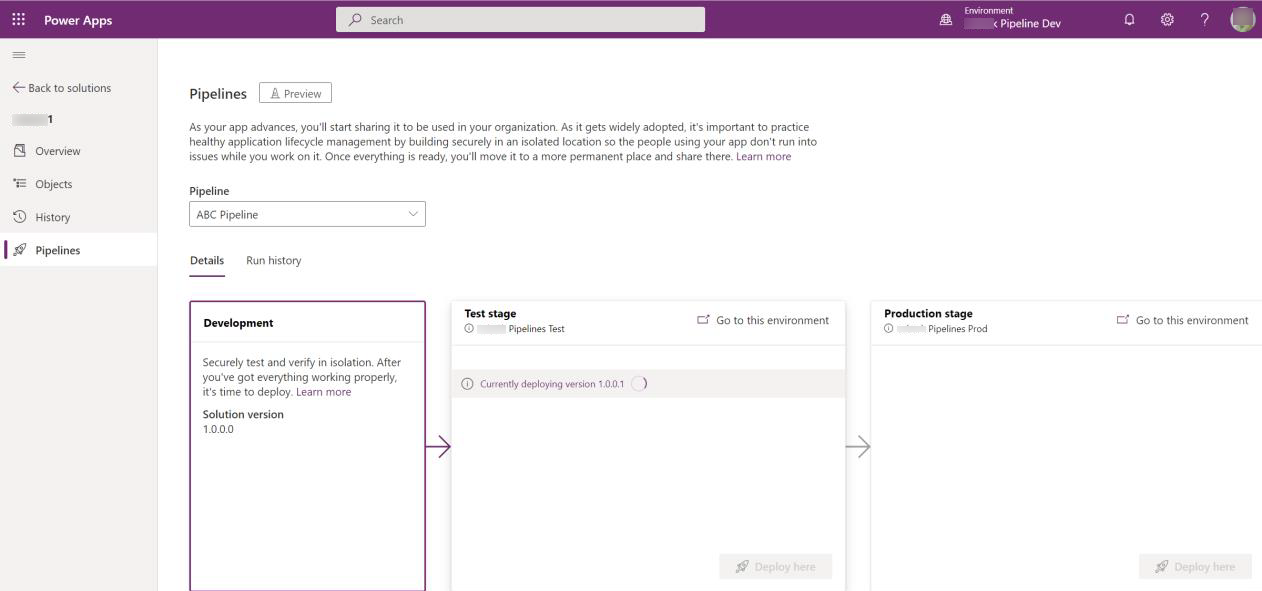
Pipelines in Power Platform
Pipelines in Power Platform aim to democratize application lifecycle management (ALM) for Power Platform and Dynamics 365 customers by bringing ALM automation and continuous integration and continuous delivery (CI/CD) capabilities into the service in a manner that's more approachable for all makers, admins, and developers. All target environments used in a pipeline must be enabled as Managed Environments.
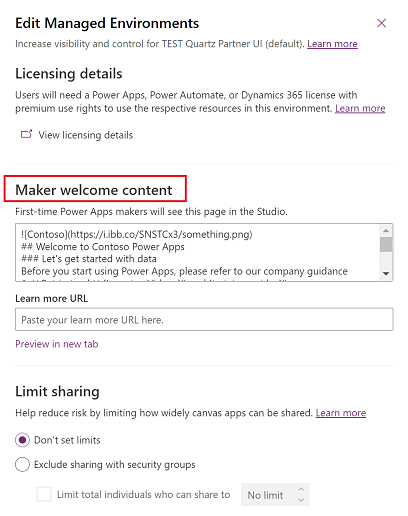
Enable maker welcome content
Admins can provide customized welcome content to help their makers get started with Power Apps. When you add your own help content, it replaces the default Power Apps first-time help experience for makers.
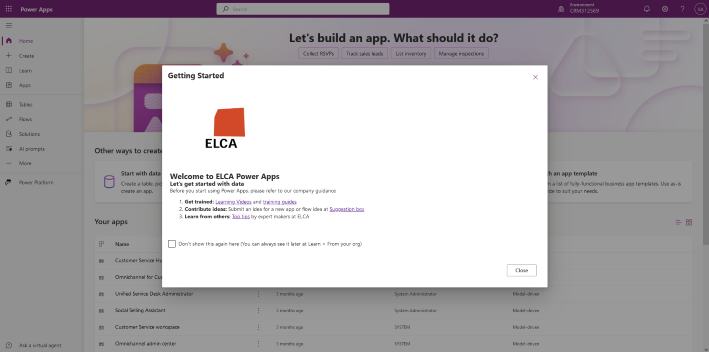
Here is an example:
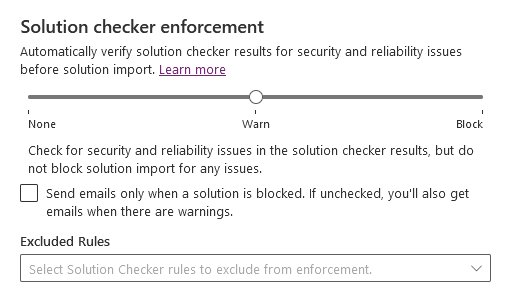
Solution checker enforcement
With solution checker enforcement feature, you can perform a rich static analysis check on your solutions against a set of best practice rules and identify problematic patterns.
| Setting | Description |
|---|---|
| None | Turns off the automatic solution validations during solution import. There aren't any experience or behavioral changes to solution authoring, exports, or imports. |
| Warn | All custom solutions are automatically verified during solution import. When a solution with highly-critical issues is being imported, you are warned about the action but the import itself continues, and if everything else with the import is fine, the solution is imported into the environment. After a successful import, a message stating that the imported solution had validation issues is shown. Additionally, a summary email is sent with details of the solution validation. |
| Block | All custom solutions are automatically verified during solution import. When a solution has highly-critical issues, the import process is canceled, and a message stating that the imported solution had validation issues is shown. This happens before the actual import, so there aren't any changes to the environment due to the import failure. Additionally, a summary email is sent with details of the solution validation. |
Who will receive the emails ?
When the validation mode is set to Warn or Block, a summary email is sent when a solution is imported or blocked. When the solution is imported into an environment, the summary email shows the count of issues by severity in the solution.
The email is sent to all users with the roles of Power Platform administrator and Dynamics 365 service administrator. It is also sent to recipients of the weekly digest emails.
By default, emails are sent for solutions containing medium or higher severities. When the checkbox "Send emails only when a solution is blocked [...]" is selected, emails won't be sent in warn mode. In block mode, emails aren't sent except for critical violations, which block solution import.
Rule exclusions
You have the option to opt out of enforcing certain solution checker rules. For instance, if fixing a specific rule requires considerable time and effort across the solution, but you still want other rules to be enforced, you can exclude that rule from enforcement. Utilize the "Excluded Rules" dropdown menu to choose which rules to exclude from enforcement. As a reminder, only critical severity rules block a solution from being imported.
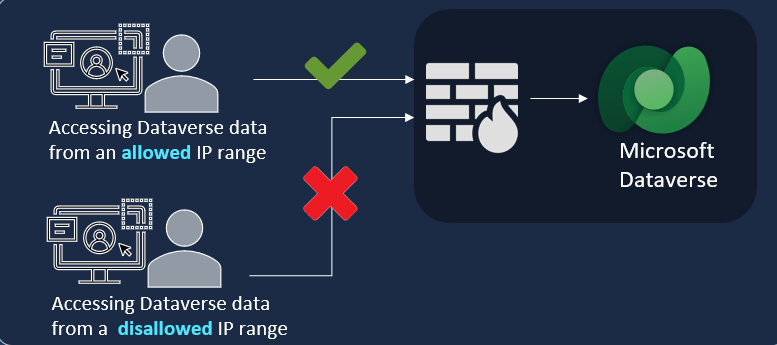
IP firewall in Power Platform environments
The IP firewall helps to protect your organizational data by limiting user access to Microsoft Dataverse from only allowed IP locations. The IP firewall analyzes the IP address of each request in real time. For example, suppose the IP firewall is turned on in your production Dataverse environment, and allowed IP addresses are in the ranges associated with your office locations and not any external IP location like a coffee shop. If a user tries to access organizational resources from a coffee shop, Dataverse denies access in real time.
Safeguarding Dataverse sessions with IP cookie binding
Prevent session hijacking exploits in Dataverse with IP address-based cookie binding. Let's say that a malicious user copies a valid session cookie from an authorized computer that has cookie IP binding enabled. The user then tries to use the cookie on a different computer to gain unauthorized access to Dataverse. In real time, Dataverse compares the IP address of the cookie's origin against the IP address of the computer making the request. If the two are different, the attempt is blocked, and an error message is shown.
Manage your customer-managed encryption key
Customers have data privacy and compliance requirements to secure their data by encrypting their data at-rest. This secures the data from exposure in an event where a copy of the database is stolen. With data encryption at-rest, the stolen database data is protected from being restored to a different server without the encryption key.
All customer data stored in Power Platform is encrypted at-rest with strong Microsoft-managed encryption keys by default. Microsoft stores and manages the database encryption key for all your data so you don't have to. However, Power Platform provides this customer-managed encryption key (CMK) for your added data protection control where you can self-manage the database encryption key that is associated with your Microsoft Dataverse environment. This allows you to rotate or swap the encryption key on demand, and also allows you to prevent Microsoft's access to your customer data when you revoke the key access to our services at any time.
Securely access customer data using Customer Lockbox in Power Platform and Dynamics 365
Most operations, support, and troubleshooting performed by Microsoft personnel (including subprocessors) don't require access to customer data. With Power Platform Customer Lockbox, we provide an interface for the customers to review and approve (or reject) data access requests in the rare occasion when data access to customer data is needed. It's used in cases where a Microsoft engineer needs to access customer data, whether in response to a customer-initiated support ticket or a problem identified by Microsoft.
Customer Lockbox is available in public clouds and US Government Community Cloud (GCC), GCC High, and Department of Defense (DoD) regions.
Back up and restore environments
For environments that don't have Dynamics 365 applications, the default backup retention period is seven days. Admins who run production Managed Environments of this type can use PowerShell to change the retention period to 7, 14, 21, or 28 days.
A Managed Environment can be restored only to another Managed Environment. A non-Managed Environment can't be restored to a Managed Environment.
Is activating the Managed Environments a risky move?
Apart from the dependence on licenses, to me, the risk associated with activating the feature is minimal, here are the reasons:
- This is transparent for the users if no feature are activated
- This option is at the environment level (not at tenant level)
- This gives more flexibility and it allows to test the features in dev environment
- Activation of a feature does not have retroactive effect
- This option can be disabled at any time
On the other hand, admins need to be careful before activating a feature because it can have an impact on users. For example, activating "limit sharing" can block user in their job. It is important to test feature before activating them in production.
When to activate Managed Environments?
- A feature requires to have Managed Environments activated
- For large organizations with lots of environments, users, apps



 Like
Like Report
Report
*This post is locked for comments