Monitoring and alerting for Azure Key Vault
 Poojith Jain
Poojith Jain
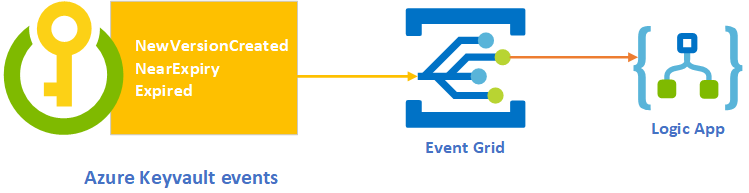
Azure Keyvault provides a secure way to store very sensitive information in the cloud. Once you have started to use a key vault to store your production secrets, it is important to monitor the key vault to make sure your service operates as intended. Keyvaults are used to store sensitive information, which is critical for the operations of connected applications. The slightest delay in the information (such as secret expiry) tracking could potentially cause a severe business disruption. A trivial example could be expired secrets, which are used to connect to multiple target applications (such D365FO, connection string to database). Expiry of these keys, secrets, and password, could cause the disruptions in applications which uses them, causing potential business disruption. The following diagram shows the high-level design for monitoring alerting expiry of secrets, keys, and Certificates.

Key Vault monitoring should also be used to ensure and audit that only allowed users; applications have access to the information they have access to. Key Vault monitoring insights provide comprehensive monitoring of your key vaults by delivering a unified view of your Key Vault requests, performance, failures, and latency.
What is Azure Key Vault?
Azure Key Vault is a cloud service for securely storing and accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, or cryptographic keys.
The azure key vault provides the option to set the expiry when we provision/store an entity in the Key Vault. We can then monitor events related to an upcoming expiry date.
- It is a secure store for entities that do require a certain level of security, for example, connection string, credentials, certificates, or other sensitive information.
- It implements a system of granular permissions that dictate which identity can access what entity, as well as who can manage sensitive information.
- It offers support for Hardware Security Modules (HSMs).
- It natively integrates with a broad spectrum of Azure and 3rd party services.
It is important to stick to Microsoft Best practices while using Azure key vault.
Alerting Key vault events
The azure key vault provides the option to set the expiry when we provision/store an entity in the Key Vault. We can then monitor events related to an upcoming expiry date. In the Azure Key vault, we can store three types of information.
- Keys
- Secrets
- Certificates
Azure Key vault provides mechanism to trigger events when the status of a secret stored in key vault has changed. Key Vault integration with Event Grid allows users to be notified when the status of a secret stored in key vault has changed. A status change is defined as a secret that is about to expire (30 days before expiration), a secret that has expired, or a secret that has a new version available. Notifications for all three secret types (key, certificate, and secret) are supported.
- NewVersionCreated: Triggers when an entity or entity version is created.
- NearExpiry: Triggers when the currents version is about to expire (30 days) as mentioned in the expiry date of the Key vault record.
- Expired: riggers when the currents version is expired as mentioned in the expiry date of the Key vault record.
| Event full name | Event display name | Description |
| Microsoft.KeyVault.CertificateNewVersionCreated | Certificate New Version Created | Triggered when a new certificate or new certificate version is created. |
| Microsoft.KeyVault.CertificateNearExpiry | Certificate Near Expiry | Triggered when the current version of certificate is about to expire. (The event is triggered 30 days before the expiration date.) |
| Microsoft.KeyVault.CertificateExpired | Certificate Expired | Triggered when the certificate is expired. |
| Microsoft.KeyVault.KeyNewVersionCreated | Key New Version Created | Triggered when a new key or new key version is created. |
| Microsoft.KeyVault.KeyNearExpiry | Key Near Expiry | Triggered when the current version of a key is about to expire. (The event is triggered 30 days before the expiration date.) |
| Microsoft.KeyVault.KeyExpired | Key Expired | Triggered when a key is expired. |
| Microsoft.KeyVault.SecretNewVersionCreated | Secret New Version Created | Triggered when a new secret or new secret version is created. |
| Microsoft.KeyVault.SecretNearExpiry | Secret Near Expiry | Triggered when the current version of a secret is about to expire. (The event is triggered 30 days before the expiration date.) |
| Microsoft.KeyVault.SecretExpired | Secret Expired | Triggered when a secret is expired. |
| Microsoft.KeyVault.VaultAccessPolicyChanged | Vault Access Policy Changed | Triggered when an access policy on Key Vault changed. It includes a scenario when Key Vault permission model is changed to/from Azure role-based access control. |
Design for Alerting events
Applications can react to these events using modern serverless architectures, without the need for complicated code or expensive and inefficient polling services. Events are pushed through Azure Event Grid to event handlers such as Azure Functions, Azure Logic Apps, or even to your own Webhook, and you only pay for what you use.
In this blog, we use Logic App to notify the status change of records stored in Key vault. The design is shown below:
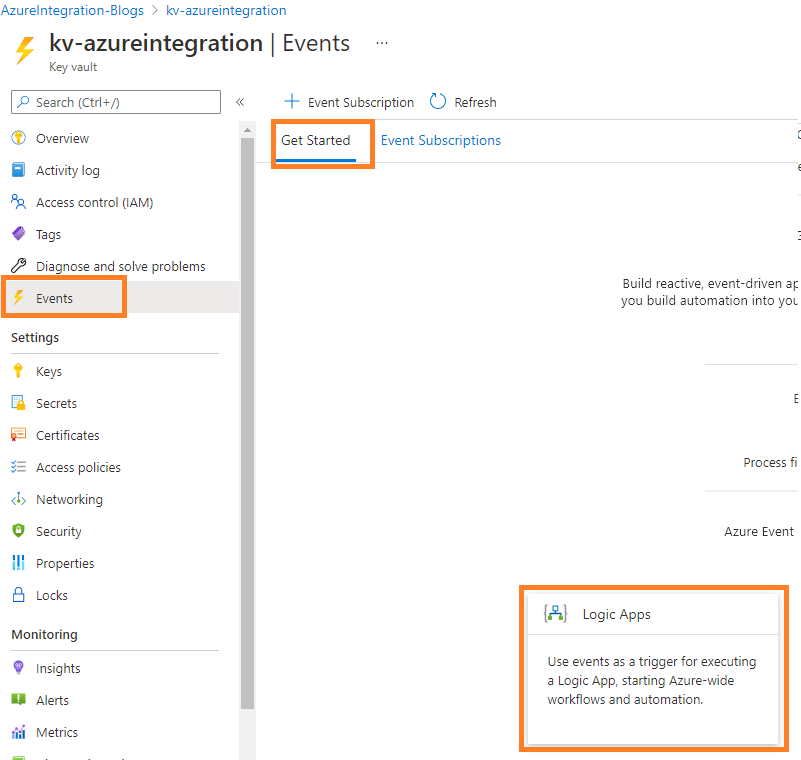
Create an Event Grid subscription
- Go to your key vault and select the Events tab, then select “Getting started”.
- Then click on the “Logic Apps”
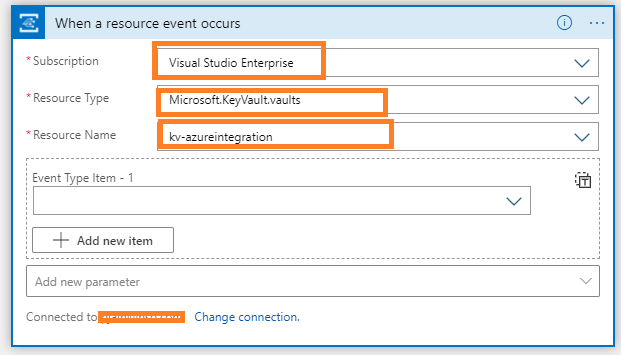
- Then configure the Event Grid Trigger with following Settings and try parameterizing these settings
- Subscription : The subscription where the key vault exists
- Resource Type: Microsoft.KeyVault.vaults
- Resource Name: Select the Key Vault which needs to be monitored.
- Click Save AS on the Logic app Designer and name the logic app and click create. Now we have a Logic App, which would listen to the events from Azure Key Vault.
- Then when we navigate to the resource group, an automatic Event Grid System Topic is created along with the Logic App. The event grid will be used to broadcast the events from Key Vault to Logic App.

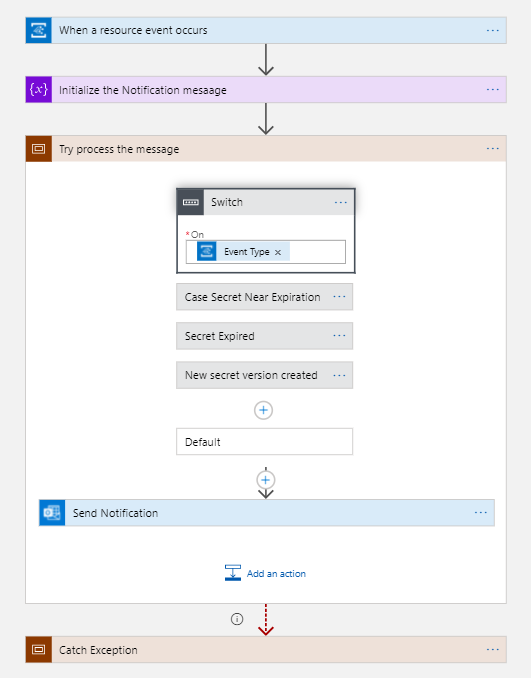
Logic App to Handle the Events from Key Vault
The Logic App gets the trigger from the Azure key vault about the status change of the records in KeyVault. The logic App can process these events and handle the event messages based on Event Type (using switch statement). Then parse and process the message and send a notification to the Administrators via email.
- Dynamics 365 FO: Priority based throttling for integrations
- Monitoring and alerting for Azure Key Vault
- Dynamics 365 UO: Set financial dimension using oData integration
- Azure Integration using Managed Identity
- D365 Finance and Operations integration using BYOD
- Azure Service Bus and Logic App integration Pattern using PeekLock
This was originally posted here.




 Like
Like Report
Report
*This post is locked for comments