Configure Internet Facing Deployment for CRM 2011 Server in more secure way with ADFS Proxy:
After reading the White Papers, blogs and YouTube videos on the topic, I figured I would need notes for myself as much as anything. This is mostly because I am yet to find one single example that covered the setup I was after. That being Separate CRM Server, DB Server, ADFS Server and ADFS Proxy(in DMZ)

Present Setup:
This is staging environment setup, with fully patched version of:
Windows Server 2008 R2 Enterprise SP1
SQL Server 2008 R2 Enterprise SP1
CRM 2011 Server
I setup CRM 2011 on the default website as ADFS is on a separate box.
Test if CRM is working on CRM Server first
Below configurations already made ready:
SAN certificate used with below entries
1) Organization Name – ifdcrm.domain.com
2) InternalCRM – internalcrm.domain.com
3) ADFS Server – adfs.domain.com
4) External Domain – authifd.domain.com
We need to have some subdomains pointing to-
CRM Server:
1) ifdcrm.domain.com
2) authifd.domain.com
3) devifd.domain.com
4) internalcrm.domain.com
ADFS Server:
1) adfs.domain.com
IIS Bindings on CRM Server
http is working on 80
add new binding with https on 443 and selected SAN certificate
- IIS Binding on ADFS Server
https on 443 and SAN Certificate
Please follow this guide and allow ports as needed. In my configuration I have allowed below firewall configuration,
To Domain: TCP domain, UDP domain, TCP 1688, TCP ldap, UDP 389, TCP 88, TCP 135, TCP netbios-ssn, TCP 445, UDP 445, UDP NTP, UDP NETBIOS-NS, UDP NETBIOS-DGM, UDP 1025, TCP 808, TCP LDAPS, TCP 3268, TCP 3269, TCP 49156, TCP 49158.
To Exchange: SMTP, 995.
TO SQL: TCP 1433, TCP www, TCP https, TCP 135, UDP 1025, TCP netbios-ssn, TCP 445, UDP ntp, UDP 445, UDP netbios-ns, UDP netbios-dgm.
To ADFS Proxy: TCP https.
To ADFS: TCP https.
To Internet: TCP https.
Configuration Claim-based authentication for internal access
1) Install and configure AD FS 2.0 .
2) Claims-based authentication configuration CRM 2011 server.
3) Claims-based authentication configuration AD FS 2.0 server.
4) Test claims-based authentication inside network.
1) Install and configure AD FS 2.0
Download the AD FS 2.0 from the following link to download the AD FS 2.0
Active Directory Federation Services
http://go.microsoft.com/fwlink/?LinkID=204237
Start installation wizard
Install prerequisites on the wizard itself.

After installation, it will automatically open ADFS Management page for the first time.
Start ADFS Configuration wizard
Click on Create new Federation Service

On next wizard , select set standalone federation server
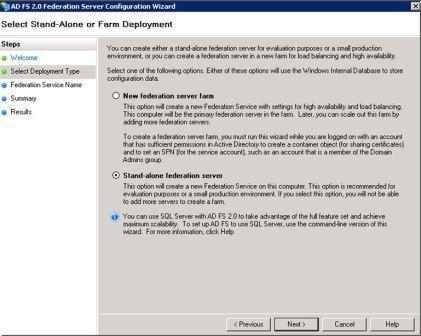
The next page you have to choose your SSL and provide federation service name

On Summary page click next
Click close.
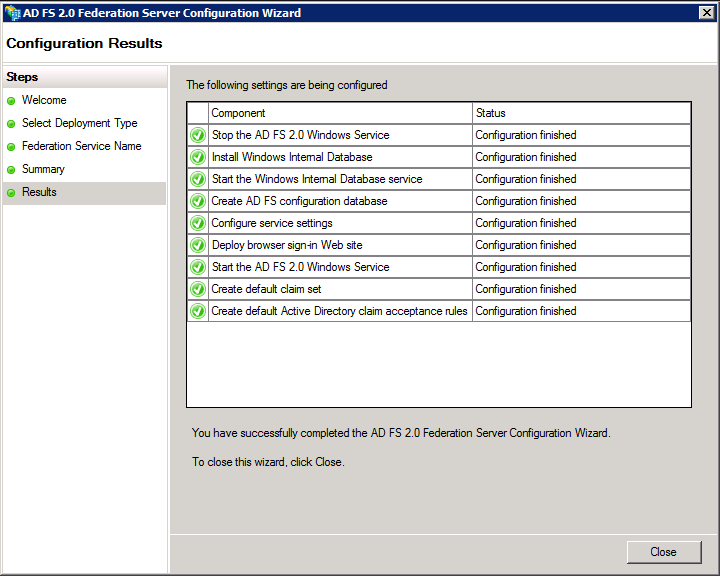
Verify ADFS Installation by checking federation metadata URL in IE. Ensure that no certificate related warning is appearing.
URL format:
https://<FederationServiceName>federationmetadata/2007-06/federationmetadata.xml

After configuring ADFS you will need to configure Claims based authentication on CRM server.
Configure Claims based authentication
Configure CRM 2011 binding to HTTPS
Go to Deployment manager on CRM Server- Right click Microsoft Dynamics CRM and hit Properties option. In Second Tab ‘Web address’ click https and provide root domain. In my case I have root domain entry ‘internalcrm.domain.com’ pointing to CRM server, and as my CRM website https binding was on port 443.

Click OK.
Provide CRMAppPool user read access on the SAN certificate kept in Private store through MMC.
Configure Claims based authentication

Click next on first page
Provide federationmetadata URL
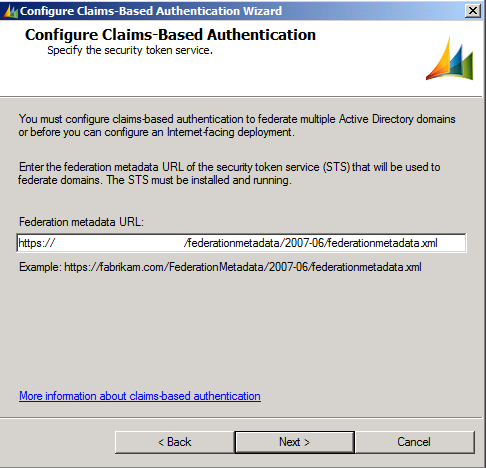
Select Certificate. Click Next

Ensure system checks passes with success, if not then you have to check Federation metadata URL is accessible without any certificate error in IE.

On next screen, click review your selection and click apply.
On final finish screen, not down the URL And if you are able to browse the same, then you are done here.
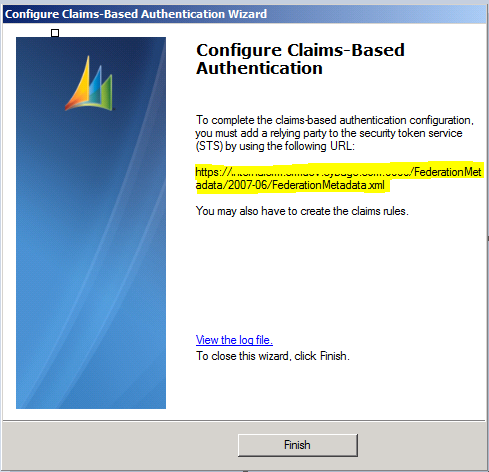
Claims based authentication configuration on ADFS Server
On AD FS 2.0, open AD FS 2.0 Management.
In the Navigation Pane , expand the Trust Relationships , and then click the Claims Provider Trusts.
In the Claims Provider Trusts under , right-click Active Directory , and then click Edit Claims Rules.
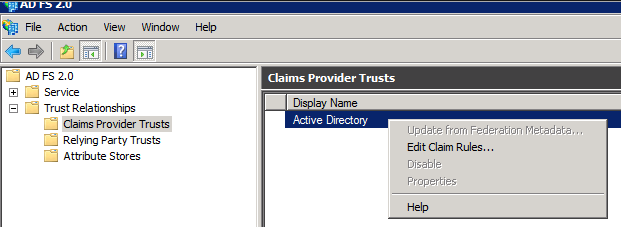
Click on Add rule
In Claim rule template list , select the Send LDAP Attributes as Claims template then click Next.

Create the rule
Claim rule name: UPN Claim Rule OR any descriptive name
Add the following mapping:
Attribute Store- Active Directory
LDAP Attribute- User Principal Name
Outgoing Claim Type: UPN

Click Finish , then click OK close the Rules Editor.
Configuration relying party trusts
Open AD FS 2.0 Management.
Under Trust relationship- Right click Add Relying Party Trust
In Add Relying Party Trust Wizard , click Start.
In the Select Data Source page , enter the federation metadata.xml file URL noted in CBA wizrd.

Click Next
In Specify Display Name page , enter a display name, such as CRM Claims Relying Party , and then click Next.
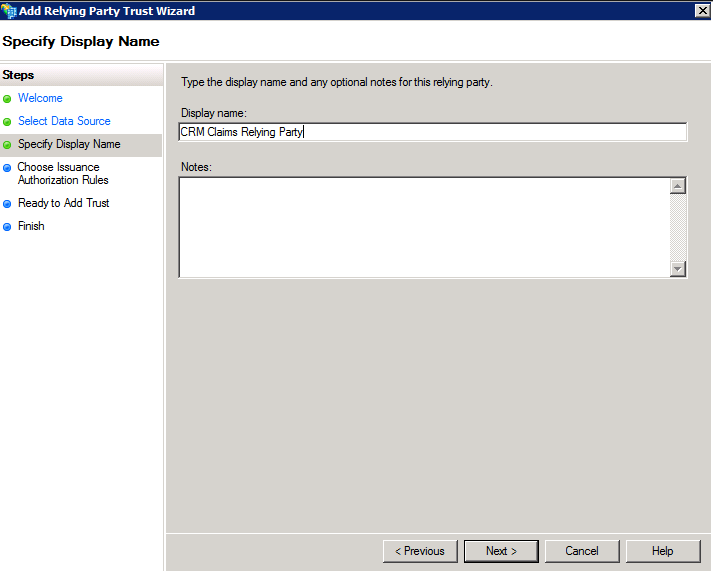
In the Choose Issuance Authorization Rules page , choose Permit All users to access this Relying Party , and then click Next.

In the Ready to Add Trust page , click Next , then click Close .
When the Rule Editor appears , click Add Rule . Otherwise, the Relying Party Trusts list, right-click you create a relying party objects, click the Edit Claims Rules , and then click Add Rule.

In Claim rule template list , select the Pass Through or Filter an Incoming Claim template, and then click Next.

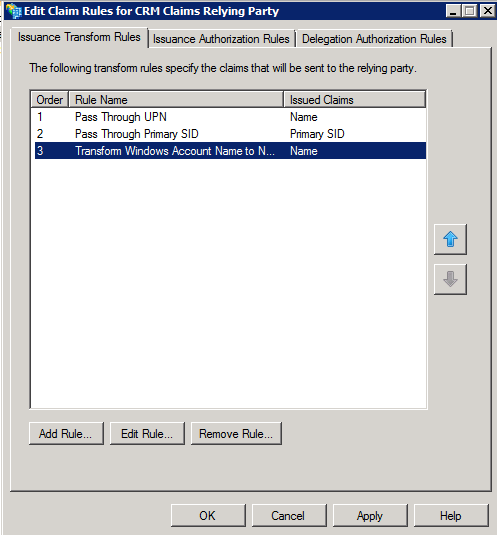
Create the following rule:
· Claim rule name: Pass Through UPN ( or other descriptive name )
· Add the following mapping:
Incoming claim type: UPN
Pass through All claim values

Click Finish .
In the Rule Editor , click Add Rule , in Claim rule template list , select the Pass Through or Filter an Incoming Claim template , and then click Next :
· Claim rule name: Pass Through Primary SID ( or other descriptive name )
· Add the following mapping:
Incoming claim type: Primary SID
Pass through All claim values

Click Finish .
In the Rule Editor , click Add Rule
In Claim rule template list , select the Transform an Incoming Claim template , and then click Next.
create the following rule:
Claim rule name: Transform Windows Account Name to Name ( or any descriptive)
Incoming claim type: Windows account name
Outgoing claim type: Name
Pass through All claim values
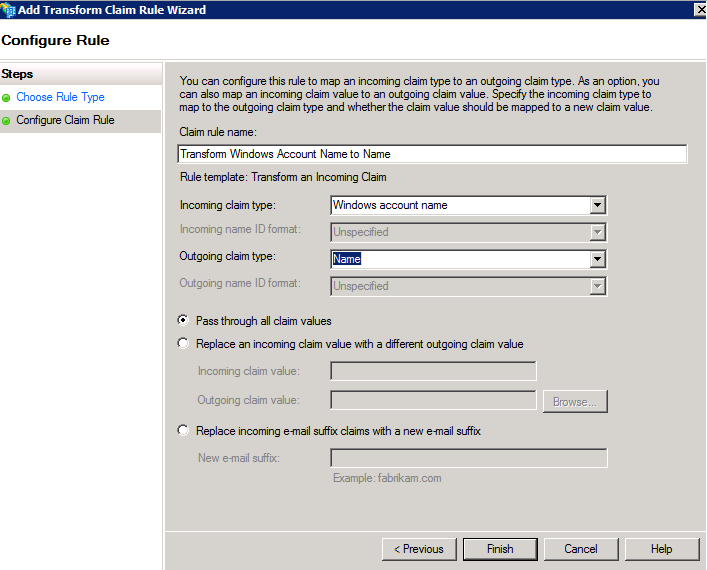
Click Finish , click OK close the Rule Editor
Test claims-based authentication within Intranet
You should now be able to use the claims certified to the internal access CRM 2011
Open the Deployment Manager.
Under Deployment Manager click on Organizations .
Right-click your organization , and then click Browse .
If you face any issue to open CRM, reset IIS.
Configuration Claim-based authentication -External access
You need to do the following steps:
- Complete contents of the previous section: Configuring Claim-based authentication- internal access.
- For the IFD configuration CRM 2011 server.
- For the IFD configuration AD FS 2.0 server.
- Test claims-based authentication external access.
IFD Configuration on CRM Server
Open the Deployment Manager.
Right-click Microsoft Dynamics CRM , and then click Configure Internet-Facing Deployment

Click Next
Fill correct domain information for the Web Application, Org, and Discovery Web services. Remembering here that in our case: *.interactivewebs.com was the name of the wildcard certificate used, and that PORT 444 was the port we configured for the CRM Web Instance in the bindings for IIS.
Thus we use:
Web Application Server Domain: interactivewebs.com:444
Organization Web Service Domain: interactivewebs.com:444
Web Service Discovery Domain: dev.interactivewebs.com:444
Note – Enter the domain name, rather than the server name .
Web Service Discovery Domain must be a Web Application Server Domain as a subdomain like the “dev.” that we setup in DNS earlier.
domain name must be on the SSL certificate name
Domain examples :
Web Application Server Domain: contoso.com
Organization Web Service Domain: contoso.com
Web Service Discovery Domain: dev.contoso.com

You must specify the domain specified in the previous step Web Application Server Domain sub-domains . default , will be “auth.” added to the Web Application Server Domain before.

Domain examples :
External Domain: auth.contoso.com
In the System Checks page , if there is no problem, click Next

In Review your selections and then click Apply page , confirm your input , and then click Apply.
Click Finish
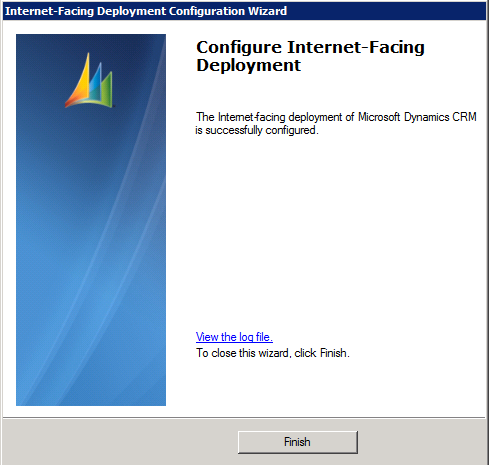
Open a command line tool, run: iisreset
The IFD configuration AD FS 2.0 server
To open CRM 2011 on the IFD , you need to add AD FS 2.0 server for the IFD to create a relying party endpoints.
Follow these steps:
open AD FS 2.0 Management .
In the Actions menu, click Add Relying Party Trust.
In the Add Relying Party Trust Wizard , click Start .
In the Select Data Source page , click Import Data about the Relying Party Online or published on a local Network , enter federation metadata.xml file URL.
Note – This is almost the same URL as we used previously, but has the .auth sub domain that we used in point above. For use the Federation metadata is configured IFD when created.
In this case https://auth.contoso.com/FederationMetadata/2007-06/FederationMetadata.xml
Check in your browser the URL, to ensure that no certificate-related warnings appear.

Click Next.
In the Specify Display Name page , enter the display name , such as CRM IFD Relying Party , and then click Next.
In the Choose Issuance Authorization Rules page , select the Permit all users to access this relying party options , and then click Next.
In the Ready to Add Trust page , click Next , then click Close .
If the Rule Editor appears , click Add Rule.OR right-click you create a relying party objects, click the Edit Claims Rules, and then click Add Rule.
In Claim rule template list , select the Pass Through or Filter an Incoming Claim template, and then click Next.
create the following rule:
· Claim rule name: Pass Through UPN ( or other descriptive name )
· Add the following mapping:
Incoming claim type: UPN
Pass through All claim values

Click OK.
In the Rule Editor , click Add Rule , in Claim rule template list , select the Pass Through or Filter an Incoming Claim template , and then click Next :
Claim rule name: Pass Through Primary SID ( or other descriptive name )
Add the following mapping:
Incoming claim type: Primary SID
Pass through All claim values

Click OK
In the Rules Editor , click Add Rule ,
In Claim rule template list , select the Transform an Incoming Claim template , and then click Next .
Create the following rule:
Claim rule name: Transform Windows Account Name to Name ( or any descriptive name )
Incoming claim type: Windows account name
Outgoing claim type: Name
Pass through All claim values
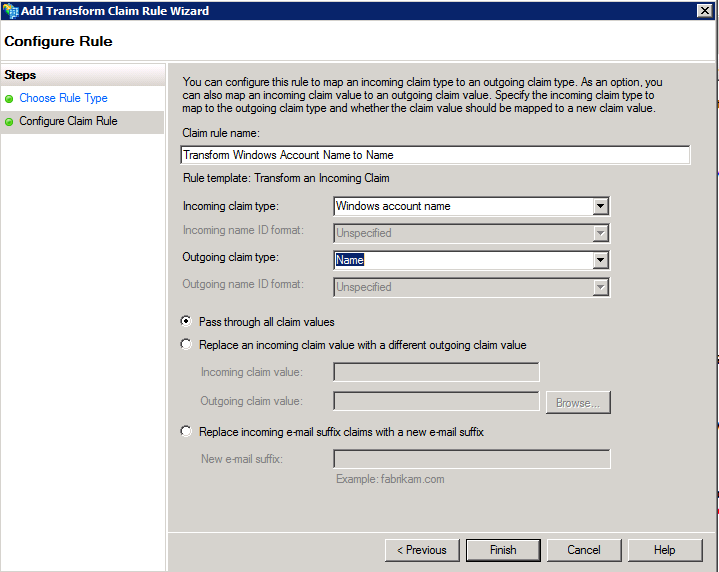
Click Ok , you have created three rule later , click OK close the Rule Editor .
Test claims-based authentication to access external
Now, you should use the claims certified external access CRM 2011 a. In IE the browser CRM 2011 external address (for example: https://org.contoso.com), you will see the following pages:

Enter the user name password, log CRM 2011.
Configure ADFS Proxy Server to redirect all traffic coming from outside network i.e. Internet
Your AD FS proxy and your ADFS servers will resolve to the same Federation Service Name. So the same SAN certificate will do work here.
Import certificate in both the certificate stores i.e. Trusted Root and Personal
Add host entry for Internal ADFS Server for example sts.contoso.com pointing to Internal ADFS and CRM Server URLs like org1.contoso.com, auth.contoso.com, dev.contoso.com pointing to CRM server which in DMZ.
Install ADFS Proxy:
Run the executable that you downloaded from Microsoft’s website “ADFSSetup.exe”.
When the “Welcome to ADFS 2.0 Setup’ screen appears, Click “Next”.

Accept the EULA agreement and Click “Next”.
Choose the “Federation Proxy” role on the “Server Role” screen and Click “Next”.
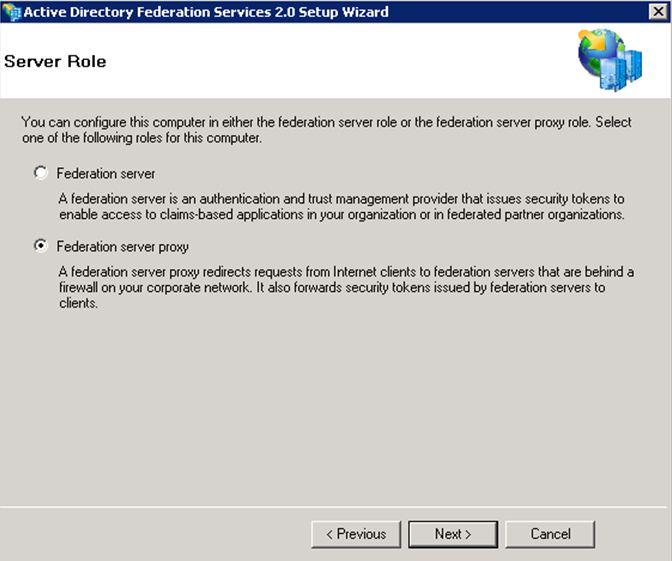
On the “Install Prerequisite Software” screen Click “Next” to install the required prerequisites for ADFS 2.0.
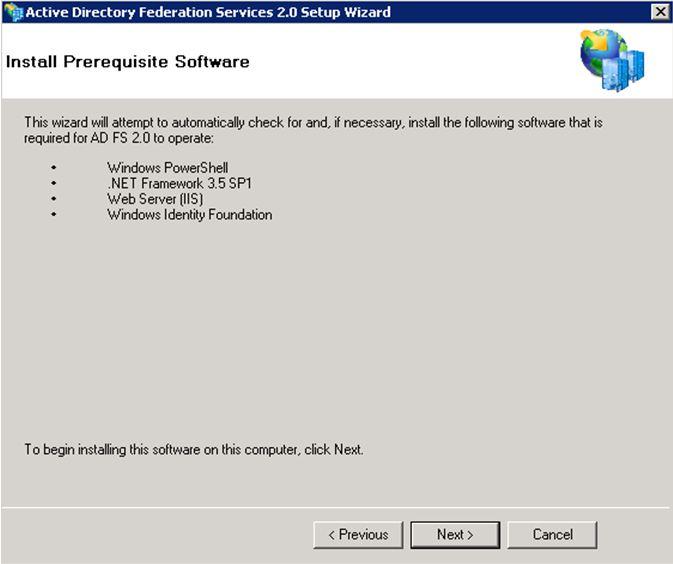
The Prerequisites and ADFS 2.0 will now begin to install as shown in the image below. Depending on the prerequisites needed, the time for the installation will vary.
Once the install is completed you will receive a completion screen for the ADFS 2.0 Setup Wizard. You can choose to start the “ADFS 2.0 Management Snap-in” when the wizard closes

Running the AD FS 2.0 Federation Proxy Server Proxy Configuration Wizard:
Open the “AD FS 2.0 Federation Proxy Server Proxy Configuration Wizard” from the Start Menu.
Click “Next on the “Welcome” screen.
On the “Specify Federation Service Name” screen, enter in the federation service name and click the “Test Connection” button. If all goes well you will see a successful connection as shown below. Click “OK” and then click “Next”.
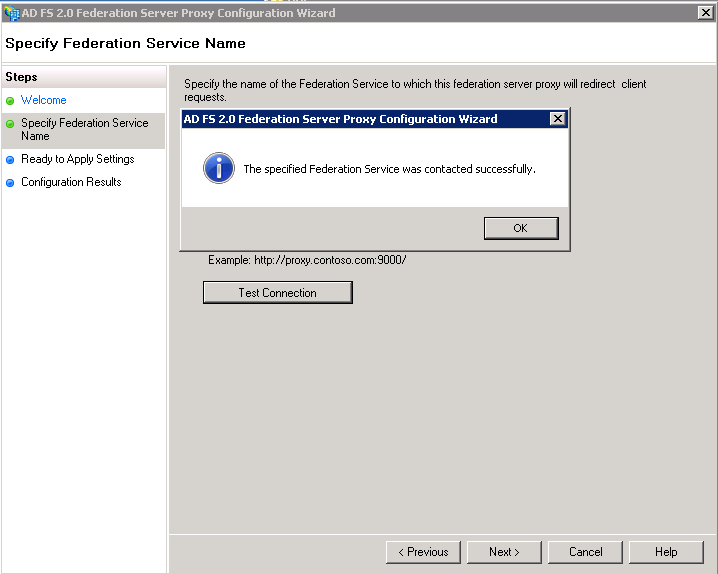
When you click “Next” on the “Specify Federation Service Name” screen you will be prompted for the ADFS Service account name that you used when configuring your internal ADFS Server Farm as shown below and click “OK”.

On the “Ready To Apply Settings” screen click “Next”.

When everything is complete on the “Configuration Settings” screen, click “Close”.

Support Websites:
http://www.microsoft.com/en-in/download/details.aspx?id=27569
Thanks,
Pradeep Pawar
Cybage Software Pvt Ltd



